Social media monitoring DOs and DON’Ts: social media marketing, social media metrics, social media monitoring tools, benchmark test, Twitter monitoring, luxury branding, and other happenings we came across while surfing the internet, blogging and posting on Facebook, Identi.ca, Google Buzz, or Twitter.
Check out previous ComMetrics weekly review posts for more tidbits, insight and intel.
The latest update is the last one at the bottom of this entry all the way down …
2010-12-03 and 05 – Update – see the risk when one outsources IT work using computing in a cloud – WikiLeaks versus Amazon (go to lower third of this post for update).
In this post, we share some interesting things we learned about who owns your digital content and what happens when you use cloud computing.
- Cloud computing and user rights
On 2010-10-04 Ricardo, the author of the blog article on Amazon Kindle Espana (a Spanish blog that reports on Amazon Kindle-related news) bemoaned the fact that Ken Follett’s book Fall of Giants, was not available for the Kindle in Spanish.
He noted that, fortunately, the publishers of the book did not mind people converting other formats, thereby enabling people to read Follett’s book in Spanish on their Kindle. Possibly to save people from having to remove the digital rights management (DRM) code to make the file work on their Kindle, the blogger linked to an already-converted copy made available on a file-hosting service.
How does cease-and-desist work?
Normally, one would expect that CEDRO (The Centro Español de Derechos Reprográficos – ‘Spanish Reproduction Rights Center’), the body in charge of collecting the levy on behalf of copyright-holders of publications in Spain, would send an email or a snail-mail cease-and-desist letter to the blog owner with a take-down request.
Instead of that, or even using the contact page, CEDRO posted the take-down notice in the comments of the article itself:

The person who posted the comment is not the same one who ‘signed’ the comment. CEDRO was surprised when nothing happened and took the matter to WordPress, saying,
Of course, leaving a comment does not mean you have tried to get in touch with a blogger, does it?
Should we care?
There are three critical things that we should reflect on before leaving this incident behind:
- 1. Get your facts straight: KindleSpain was not hosting any copyrighted works since the page only carried a link to a copyrighted work. Under Spanish law (tested on countless occasions within the last two years before Spanish magistrates), this is completely legal, since the blog makes no direct profit from any infringement.
- 2. Check and re-check: WordPress did not check with the blog owner before taking the blog post offline. Nor did it ensure that the claim made by CEDRO presented the facts truthfully (we tried – no response, etc.).
- 3. Cloud computing as a service: This case illustrates the risks when outsourcing hosting of data services. If the hosted service provider fails, your business suffers. Amazon also showed a distinct lack of respect for its users when it removed over 1 million copies of a book from their Kindle devices without telling them first.
Adding insult to injury, the first user comment on the blog points out that the link fails to work.
What you think? Do you agree that cease-and-desist letters should be sent via email or as a comment on a blog post. Did WordPress do the right thing?
- 2010-12-03 and 05 – Update – WikiLeaks, Schweizer Piratenpartei (PPS) vs. Amazon and EveryDNS.net
This update shows the risks one faces when deciding to outsource IT applications and servers using computing in a cloud – WikiLeaks versus Amazon
It began when EveryDNS.net, a service that translates online addresses to Internet Protocol numbers to provide access, ended WikiLeaks’ service at 03:00 hours GMT. This resulted in the webpage being unavailable for several hours. See EveryDNS’ reasoning for cutting WikiLeaks’ service off below.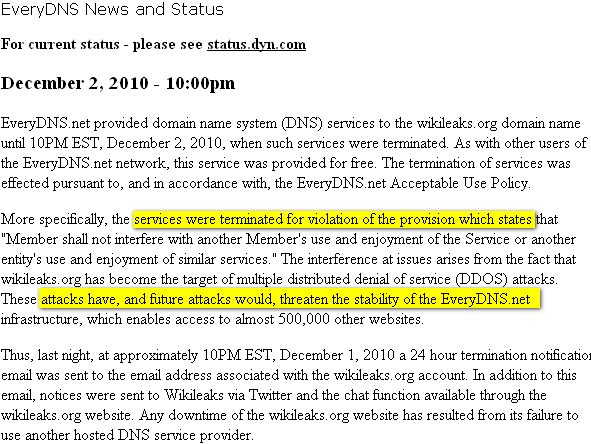
 The above user policy does allow EveryDNS.net to claim that the user is violating policy in such a case as WikiLeaks servers being exposed to a denial-of-service attack. What this implies is that Wikileaks is being held liable/responsible for a possibly illegal act by an unknown party. This is surely neither just, fair nor according to US law is it?
The above user policy does allow EveryDNS.net to claim that the user is violating policy in such a case as WikiLeaks servers being exposed to a denial-of-service attack. What this implies is that Wikileaks is being held liable/responsible for a possibly illegal act by an unknown party. This is surely neither just, fair nor according to US law is it?
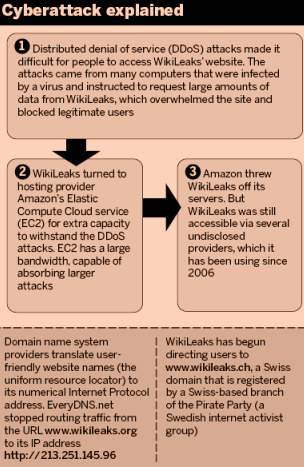
In response, WikiLeaks began directing users to its Swiss domain: WikiLeaks.ch. Unfortunately, the Swiss Domain failed to work more than a couple of hours because the Schweizer Piratenpartei (PPS) or Swiss pirate party (the owner of the WikiLeaks.ch domain) had also used EveryDNS.net to translate its address into Internet Protocol Numbers (e.g., Wikileaks.org = 213.251.145.96).
But with the help of some smart hopscothcin to avoid hacking attacks, WikiLeaks.ch is up again.
Incidentally, EveryDNS.net applied the same reasoning as shown above for the WikiLeaks.org domain to the .ch one and stopped the service, until things got fixed by the domain owners.
Today, Swiss Federal Police began checking if any content shown on WikiLeaks.ch violates any Swiss laws. But it seems that it will be difficult to prove any wrongdoing under Swiss legislation. Hence, some politicians have gone public, stating that it is unlikely that a Swiss court would support the government’s request (if it were forthcoming) to order Switch (the Swiss domain registrar) to block the address.
Please subscribe with your e-mail below, you will get the next blog post first.
- What does this mean for your IT application and database managed in the cloud?
This case raises an important concern regarding risk management and using computing in a cloud. Amazon Web Services decided to shut down the computing in a cloud service it had provided to its paying customer WikiLeaks based on its interpretation of the latter having violated its user policy. But what recourse does WikiLeaks or any cloud computing customer have in a case like this?
This is not an unfair question since Amazon has a track record of deciding against customers when the going gets tough. We remember George Orwell’s 1984 book. Amazon decided to remove it from more than 1mio customers’ Kindle without informing them beforehand. The company explained that the book had been added to the Kindle store by a company which did not have rights to it. We reported about this and outlined the property rights issues.
- Who owns your data in a cloud or on a Kindle for that matter?
Is it the cloud computing provider or the client that paid for the digital content he downloaded onto an iPod. What about the company whose application is outsourced using cloud computing. Does it own those data and which country’s laws apply in case of privacy, compliance and liability matters (e.g., if parts of these data are stored in Ireland, US or India)?
The WikiLeaks incident raises awkward questions for advocates of cloud computing and Amazon Web Services (AWS) itself. Under what circumstances does AWS feel justified in shutting down a customer. This could happen to your application, so read on.
AWAS claims that it was not due to denial-of-service attacks against WikiLeaks’ servers that made it decide to shut the service down as the copy of its statement below illustrates.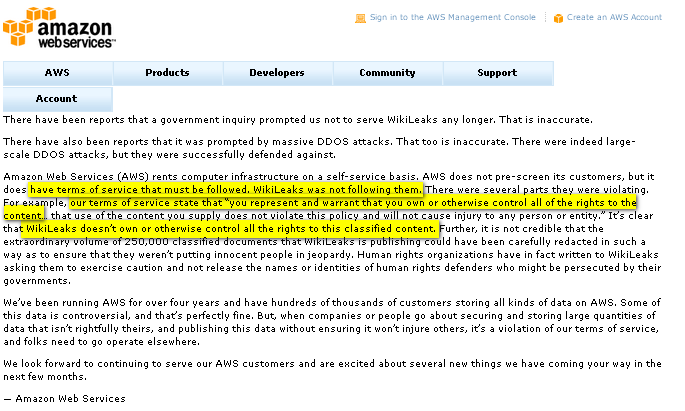
But if the above is the reason:
- 1. What does this mean if your public-facing application in the cloud experiences such an attack?
2. Will you be shut down based on a stringent user policy that gives the company the right to cut you off?
3. What about a case where a party claims that you do not own or otherwise control all rights to some information? Will Amazon, Google, Microsoft or whoever provides the service first shut you down before giving you a chance to clarify the matter?
One would expect that the application’s owner with AWS together find a way to shut out the attacks or shift operations to a dedicated and protected server. But as questions 2 and 3 above suggest, if there is a disagreement, the one that owns the server and infrastructure has the key to shut you down. Not encouraging.
- A – How big is this risk?
B – How prepared is your application hosted in the cloud for such a scenario?
This case confirms that possession is nine-tenths of the law. Are the possible cost savings worth the risks taken to have one’s services shut down? What is your opinion?
- Article source: ComMetrics weekly review: Cloud computing, WikiLeaks and Amazon
Pingback: InfoSec
Pingback: World Economic Forum
Pingback: WhitePapers
Pingback: MyComMetrics
Pingback: Urs E. Gattiker
Pingback: CyTRAP
Pingback: Urs E. Gattiker
Pingback: MOLOTOV
Pingback: CloudHosting
Pingback: World Economic Forum
Pingback: InfoSec
Pingback: MyComMetrics
Pingback: Urs E. Gattiker
Pingback: 2011 trends: Risk management and social media ROI » social media monitoring, social media marketing, Twitter monitoring, Facebook strategy, social media ROI, customer engagement, customer relationship management, » Helping you benchmark smarter to incre
Pingback: Urs E. Gattiker
Pingback: InfoSec
Pingback: World Economic Forum
Pingback: angelserendib
Pingback: Naijand Inc
Pingback: Naijand Inc
Pingback: ComMetrics weekly review: Facebook, Naoto Kan and Fortune 500 blogs » Wikileaks, social media monitoring, social media marketing, best practice, Twitter monitoring, benchmark test, Facebook strategy, customer engagement » Helping you benchmark smarter t
Pingback: ComMetrics weekly review: Cloud computing and cyber-wars » risk management, risk assessment, denial-of-service, DDoS, WikiLeaks, social media monitoring, social media marketing, Twitter monitoring, Facebook strategy, social media ROI, customer engagement
Pingback: ComMetrics weekly review: Trendy social media » risk management, risk assessment, denial-of-service, DDoS, WikiLeaks, social media monitoring, social media marketing, Twitter monitoring, YouTube dashboard, Facebook strategy, social media ROI, customer en
Pingback: 2011 trends: Web lovers and privacy - social media monitoring, social media marketing, privacy management, data protection, risk management, Facebook strategy, social media ROI, customer engagement, customer relationship management, - CyTRAP Labs provides